CLIs are very powerful, from the tip of fingers, you can quickly make the computer do anything you want. No need to wave your mouse around, hoping to find the right sub-sub-sub-menu where the feature you want is implemented. But it comes at a cost: for each command, you need to know how to write (…)
The health and well-being of our visitors, partners, employees and suppliers are at the heart of our concerns. Faced with a very changing situation, the FIC organisation team is fully mobilized, in constant contact with the competent authorities and all the people involved, to welcome you all in the best possible sanitary conditions. In this (…)
I found this nice twitter thread from Vitalik Buterin, the inventor of the Ethereum blockchain: Doing a random twitter experiment just on this day. Only the 268 people I follow can reply to this tweet. Feel free to ask things and I'll talk about anything crypto or non-crypto related. — vitalik.eth (@VitalikButerin) September 1, 2021 (…)
NaCl is one of the most used cryptography library around, and it is understandable: it is easy to use (it hides the crypto-magic used), portable (via the libsodium fork), and available in many languages. It is used by one of the project we are helping, drop, written in Rust, which we want to partially run (…)
RegHorizon and ETH Zurich’s Center for Law and Economics have partnered since 2019 to create an unbiased platform for a timely multi-stakeholder discussion among policy makers, academia, business and society focusing on challenges that AI technologies pose and exploring relevant policy solutions to address them.
The 2nd AI Policy Conference continues the multi-stakeholder dialogue started last year with leading experts to explore the use of public policy and societal engagement to capture the benefits of artificial intelligence, minimize its risks and enhance its adoption.
For more information click below.

Concurrent programming is one the oldest and hardest issues in the Computer Science Book. For years, we have been using locks, big threads sharing the minimum, using optimistic reasoning for “how data will be updated”. And we are still stuck with the same issues of some part of the code “failing” to use the updated object, dead and soft locks with hard-to-see origins, and many many crashes.

The article Why Blockchain Is Not Yet Working goes over six points – for most of these points, research papers exist. For some of them test networks exist. Only one or two are solved in active main networks.

This conference will take place on October 15th, 9:00-17:00, at the Maison de la Paix of the Graduate Institute, Geneva (IHEID). It will address a number of key questions: How does a lack of digital trust manifest itself today? Is this justified, based on current privacy and security issues, or is it exaggerated? Understated? What lessons can be learned from other sectors on how to build the trust that will be needed for our digital future. What is possible in the digital future, and what will be lost without digital trust? And finally, how should that digital trust be built?
The event is jointly organised by IHEID’s Centre for Trade and Economic Integration (CTEI) and EPFL’s Center for Digital Trust (C4DT).
For more information click below.

To promote research and education in cyber-defence, EPFL and the Cyber-Defence Campus have jointly launched the “CYD Fellowships – A Talent Program for Cyber-Defence Research.” The fourth call for proposals is now open with a rolling call for Master Thesis Fellowship applications, and with a deadline of 16 August 2021 for Doctoral and Distinguished Postdoctoral Fellowship applications. CYD fellows are hosted by a higher education institution in Switzerland and conduct their research at the CYD Campus located on the premises of EPFL and ETHZ and in its office in Thun. For more details visit the program’s dedicated website by clicking the link below or join the online Applicant Workshop on 5 August 2021 from 10.00 to 10.45 CEST (for more information please contact research@epfl.ch).
If weakening encryption through legislation or judicial orders is not the right solution, are there other ways to reconcile privacy, security and public safety? How can policymakers ensure a coherent approach on apparently divergent policy objectives? What can the EU do to promote encryption? Can government agencies develop new investigative techniques without undermining encryption?
Women in Cyber is specifically targeted towards women in security. It will be held virtually on June 10th and will be made up of a number of presentations from women across Switzerland who work in this field, from NCSC, SWITCH, Deloitte, Kudelski Security, ETH, Microsoft, Swiss Re, UBS and Trend Micro. It will close with an address from our Federal Councilor and Head of the Department of Defense, Viola Amherd.

The certificate linked to the virus will not be available before June in Switzerland. Until then, here are twelve answers linked to questions of security, data and accessibility concerning what some call the “Immunity Passport”. In particular, Jean-Pierre Hubaux, C4DT Academic Director, provides insights on the questions linked to data.
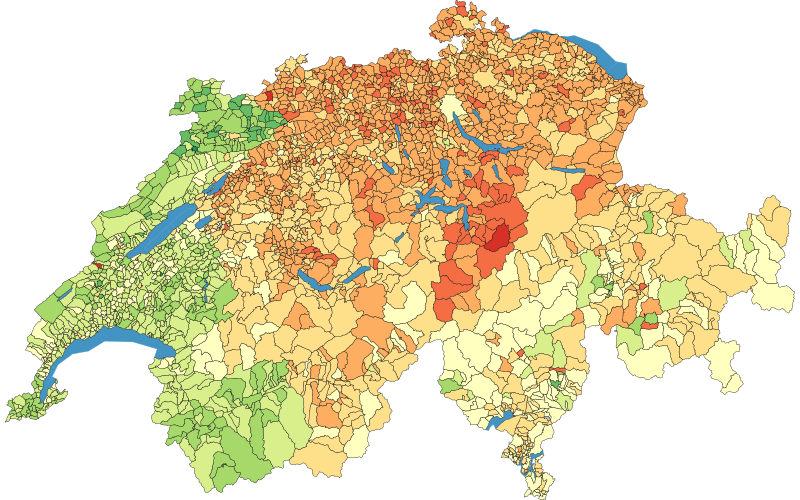
On the 7th of March, the Swiss population voted on a ban for full face coverings, the e-ID Act, and an economic partnership agreement with Indonesia. As with all Swiss referendums since 2019, the EPFL election prediction tool Predikon generated real-time predictions for the vote outcomes.
In communication systems, there are many tasks, like modulation recognition, for which Deep Neural Networks (DNNs) have obtained promising performance. However, these models have been shown to be susceptible to adversarial perturbations, namely imperceptible additive noise crafted to induce misclassification. This raises questions about the security but also the general trust in model predictions. In this project, we propose to use adversarial training, which consists of fine-tuning the model with adversarial perturbations, to increase the robustness of automatic modulation recognition (AMC) models. We show that current state-of-the-art models benefit from adversarial training, which mitigates the robustness issues for some families of modulations. We use adversarial perturbations to visualize the features learned, and we found that in robust models the signal symbols are shifted towards the nearest classes in constellation space, like maximum likelihood methods. This confirms that robust models not only are more secure, but also more interpretable, building their decisions on signal statistics that are relevant to modulation recognition.
Cyber security information is often extremely sensitive and confidential, it introduces a tradeoff between the benefits of improved threat-response capabilities and the drawbacks of disclosing national-security-related information to foreign agencies or institutions. This results in the retention of valuable information (a.k.a. as the free-rider problem), which considerably limits the efficacy of data sharing. The purpose of this project is to resolve the cybersecurity information-sharing tradeoff by enabling more accurate insights on larger amounts of more relevant collective threat-intelligence data.
This project will have the benefit of enabling institutions to build better models by securely collaborating with valuable sensitive data that is not normally shared. This will expand the range of available intelligence, thus leading to new and better threat analyses and predictions.
Current digital trends and innovation, including artificial intelligence, cybersecurity, data privacy, blockchain and digital trust, are rapidly changing and disrupting the way donors, employees, and beneficiaries interact with each other. Technology can be a powerful tool for philanthropic and non-profit organizations, accelerating their digital transformation through automating and streamlining business processes, using digital platforms, and leveraging data and analytics in new ways that enhance their efficiency and social impact.

The ease of creating fake virtual identities plays an important role in shaping the way information—and misinformation—circulates online. Social media platforms are increasingly prominent in shaping public debates, and the tension between online anonymity and accountability is a source of growing societal risks. This article outlines one approach to resolving this tension, with “pseudonym parties” that focus on proof of personhood rather than identity. Pseudonym parties are a low-tech approach to important digital challenges, linking online activity to anonymous digital tokens that are obtained by being physically present at an appointed time and place.
Ten years ago CRITIS 2011 was held in Lucerne. On September 27, 28 & 29, 2021, the 16th International Conference on Critical Information Infrastructures Security (CRITIS 2021) will be back in Switzerland and take place at the EPFL SwissTech Convention Center. CRITIS 2021 aims to bring together researchers, professionals from academia, critical (information) infrastructure operators, industry, defence and governmental organizations working in the field of critical infrastructures protection (CIP).
This Monday I presented the following article. It discusses blockchains shortcomings. Even if it has been written in 2018, it is still very up-to-date… What follows here is a very opinionated piece. As such it reflects the journey I did in blockchains over the past 6 years. And I’m sure I missed out a lot (…)
Concurrent programming is one the oldest and hardest issues in the Computer Science Book. For years, we have been using locks, big threads sharing the minimum, using optimistic reasoning for “how data will be updated”. And we are still stuck with the same issues of some part of the code “failing” to use the updated (…)
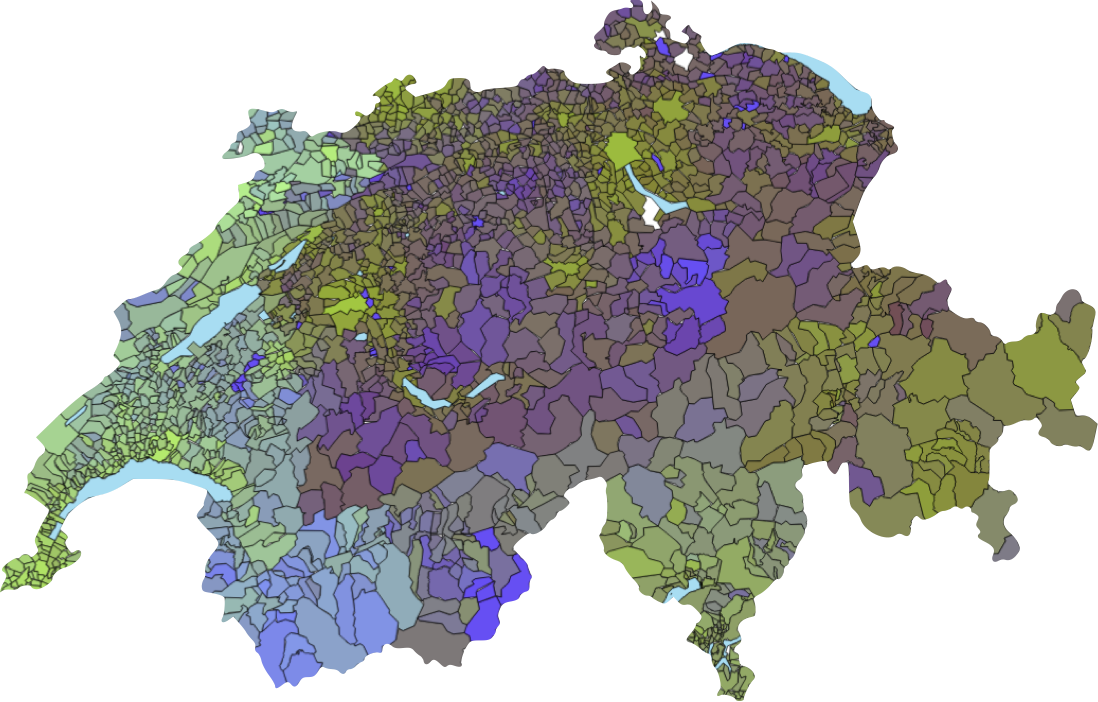
On March 7, the next Swiss referendum vote will be held, with votes on a ban for full face coverings, the e-ID Act, and the economic partnership agreement with Indonesia. As this national vote approaches, the EPFL election prediction tool, Predikon, is rolling out some improvements with new features.
We’ve been looking at the very nice https://gather.town and played around with it. Instead of having a fixed view of all participants, you can walk around and ‘meet’ different persons in gather.town. You can edit the space your liking. It looks very much like a very old-school Zelda: What I liked a lot about it (…)
The management of IT infrastructure is a constantly evolving topic. A very interesting concept that emerged in the last decades is the idea of infrastructure as code: instead of configuring servers in an artisanal fashion, the process is formalized into definition files, which are then automatically “executed”. There are multiple advantages, notably: The files always (…)
Code formatting is the most known instance of bikeshedding: everyone has a different opinion on it and nobody is willing to compromise. Do you remember the hours-long discussions on using tabs versus spaces? Where to add empty lines? Alignment of fields? For some years now, many languages provide their own code formatter, Go has gofmt, (…)







